Update: Not dead.
YO!
I realized it’s been quite a while since the first ever article got posted back in july. Well, the bubble is still alive and definitely not dead. Stay tuned for more articles to come.
OKAY! With that out of the way, let’s now dive into the real meat of the matter.
Step into the ring!
Hack The Box is an incredible time investment if you want to dip your toes into the world of penetration testing. You get access to high quality machines of varying difficulty to hack on all in a legal and gamified way.
TIER 0: EXPLOSION
We’re going to hack on one of their Starting Point machines. These are beginner-level machines ranging in tiers that every fresh novice on the platform (and those stepping into the field) is recommended to start from. The machine is called explosion and the operating system will be Windows.
Task 1:
What does the 3-letter acronym RDP stand for?
Remote Desktop Protocol
Ex: RDP is a proprietary protocol built by Microsoft that allows users to connect to another computer over a network connection. Connected users are then granted access to resources of that computer as if they had physical access to it. Be sure to know that RDP operates on TCP/UDP port 3389.
Task 2:
What is a 3-letter acronym that refers to interaction with the host through a command line interface?
CLI
Ex: The command-line offers a more traditional tried and true interaction with the OS and it’s applications. Command-line applications generally have less latency and less data transfer overhead making it more preferable for both the client and server.
Task 3:
What about graphical user interface interactions?
GUI
Ex: Graphical user interfaces are the most common way (and generally the most sane way) of interacting with a computer OS and it’s guts.
Task 4:
What is the name of an old remote access tool that came without encryption by default and listens on TCP port 23?
telnet
Ex: Telnet can be thought of as a less secure version of SSH.
Task 5:
What is the name of the service running on port 3389 TCP?
ms-wbt-server
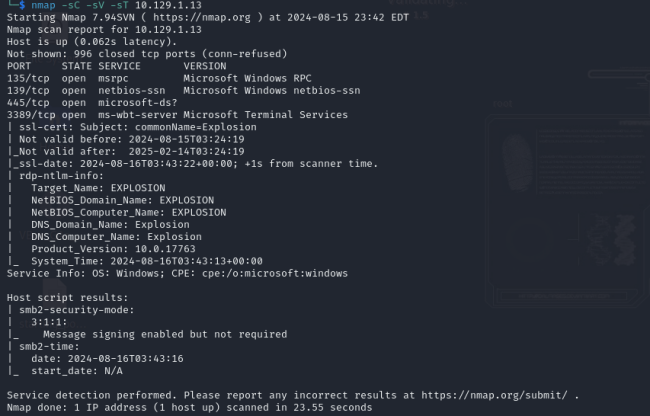
Ex: After running our nmap scan on the target machine, we discovered a Microsoft Remote Desktop service running on port 3389.
Task 6:
What is the switch used to specify the target host’s IP address when using xfreerdp?
/v:
Task 7:
What username successfully returns a desktop projection to us with a blank password?
Administrator

Ex:
/cert:ignore will ignore all security certificate requirements.
After upon trying many different usernames, we’re able to gain a foothold with Administrator.
Task 8:
Root flag:
951*****************************
Ex: After a remote GUI connection has been established, we now have access as Administrator and with the flag file sitting in plainsight!
Tag(s): [By: Abe] [Cybersec] [Hack the Box] [Updates]